Operations of an APT malware written in PureBasic
My previous post was about a maldoc which dropped a malware using strings stored as values of various OLE form fields. The dropped malware is written in PureBasic. There are very few public reports about malware written in PureBasic.
The operations of the dropped malware are presented here. It has basic remote access capabilities such as running commands remotely, and installing additional files/malware as desired by the threat actors. This malware probably belongs to North Korean Lazarus APT Group.
Malware characteristics
The file is a 64-bit PE exe and has a compilation timestamp of 2021-11-07 06:46:03 UTC. It is compiled with PureBasic 4.X compiler.
Most of the strings used by the malware, including the C2 server address, are stored with XOR encryption using the key n>t#8;S< followed by base64 encoding, and are decrypted at runtime as needed. The malware contains multiple long Sleep() calls, some of which have randomly generated delays.
The C2 IP address 40[.]121[.]90[.]194 runs a web server and the malware communicates with it via POST web requests over HTTP.
A 32-bit version of this malware, compiled 4 seconds before this one, is also present on VirusTotal.
POST request format
The malware sends POST requests to C2 at path /help.php. It uses Mozilla/5.0 (Windows NT 10.0 WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/62.0.3202.9 Safari/537.36 as the User Agent string.
The POST request body can contain upto four parameters:
-
id (required): Eight hex digits (4 bytes) CRC32 checksum of a concatenated string formed from MAC address, System Name and IP address of the victim system. It is used as an ID as well as a XOR key for encrypting query and rep0 POST parameter values.
-
page (optional): Two digit code indicating status of last response received from C2. Possible codes and their meanings are given at the end of the post.
- query (required): Encoded and XOR encrypted string containing basic system information. Following values are first concatenated with a pipe
|symbol between values:- IP address
- System Name
- User Name
- #PB_OS_Windows enum value (equals 110 on Windows 10, for example)
- OS bitness (64 for 64-bit, 86 for 32-bit)
The string is then XOR encrypted with id value, base64 encoded and finally URL encoded.
- rep0 (optional): Encoded and XOR encrypted string containing output of last command received from C2. The string contains the command (with arguments, if any) followed by a line of 40 hyphens
-followed by the command output on a newline. The total length of this string must be at least 54 characters for rep0 to be included in the POST request. Like query value, this string is also XOR encrypted with id value, base64 encoded and then URL encoded.
C2 response format
If the C2 server returns HTTP response status code 504, the malware deletes itself with command cmd /c ping /n 3 127.0.0.1 > NUL & del /q /f <filename>.
HTTP response status code 500 is sent for regular operations of the malware. In this case, the POST response body contains instructions from the server.
A sample POST response from the C2 is shown below:
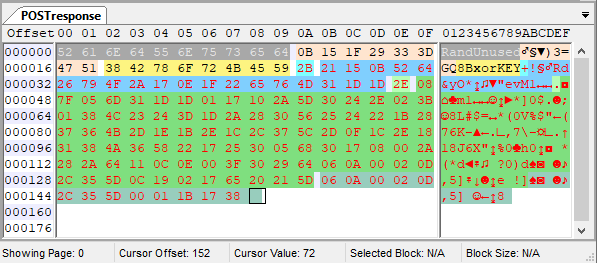
- Unused 10 bytes: The POST response body starts with 10 random unused bytes.
- 8 byte signature: The next 8 bytes from 0xA to 0x11 are a fixed signature. These bytes must be [0x0B, 0x15, 0x1F, 0x29, 0x33, 0x3D, 0x47, 0x51] for the response to be considered valid. The bytes are [11, 21, 31 .. 81] in decimal.
- 8 byte XOR key: The 8 bytes from 0x12 to 0x19 are used as a XOR key. The remaining bytes in the POST response are XOR encrypted with this key.
The same POST response with bytes from 0x1A decrypted with XOR key are shown below:
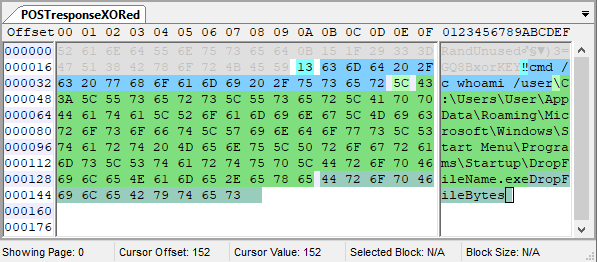
The meaning of remaining bytes after XOR decryption is as follows:
- 1 byte command string length: Byte 0x1A has value equal to length of command string (with arguments, if any) which starts from the next byte.
- Command string with arguments: Bytes starting from 0x1B represent a command to be executed by the malware. The substring after first space in the string is used as argument for the command. The output of the command is sent to the C2 server in next POST request as value of rep0 parameter.
- 1 byte drop file path length (optional) : The next byte (if present) after command string has value equal to length of drop file path string which starts from the next byte.
- Drop file path (present only if drop file path length byte is present) : These bytes represent a path with filename for a file to be dropped on the system.
- Drop file bytes (present only if drop file path string is present) : The remaining bytes following the path string are the bytes of the file to be dropped on the system.
The malware creates a temporary file in %TEMP% directory, writes the POST response body into the file and then parses the response. The name of the temporary file is n.tmp where n is a random number between 100 and 999. The file is deleted before the next POST request is sent.
Any file dropped by the malware is hidden and timestomped to match the timestamps of c:\windows\system32\explorer.exe. It may be noted that explorer.exe does not exist in system32 folder on 64 bit Windows systems. The timestamps are set to Epoch zero (1 January 1970 00:00:00 UTC) in this case.
If the dropped file’s name ends with “exe” or “EXE”, 40000000 (~38 MB) random bytes are appended to the file.
page status values
Possible values of page POST parameter along with their meaning are given below:
| Value | Meaning |
|---|---|
| 13 | Successfully parsed and executed last response |
| 20 | Error. Response data body has length <=1 |
| 21 | Error. Response data body has length from 2 to 27 |
| 22 | Error. 8 byte signature (from bytes 0xA to 0x11) is missing |
| 23 | Error. Length of command string is less than expected |
| 24 | Error. Length of drop file path string is less than expected |
| 25 | Error. Could not create temporary file for writing POST response body |
| 11 | (Temporary) Set internally during processing of response by the malware |
Except what is described above, the malware has no other functional capabilities.